‘If you want to protect yourself then the devil really is in your details’ – Jac sm Kee, APC Women
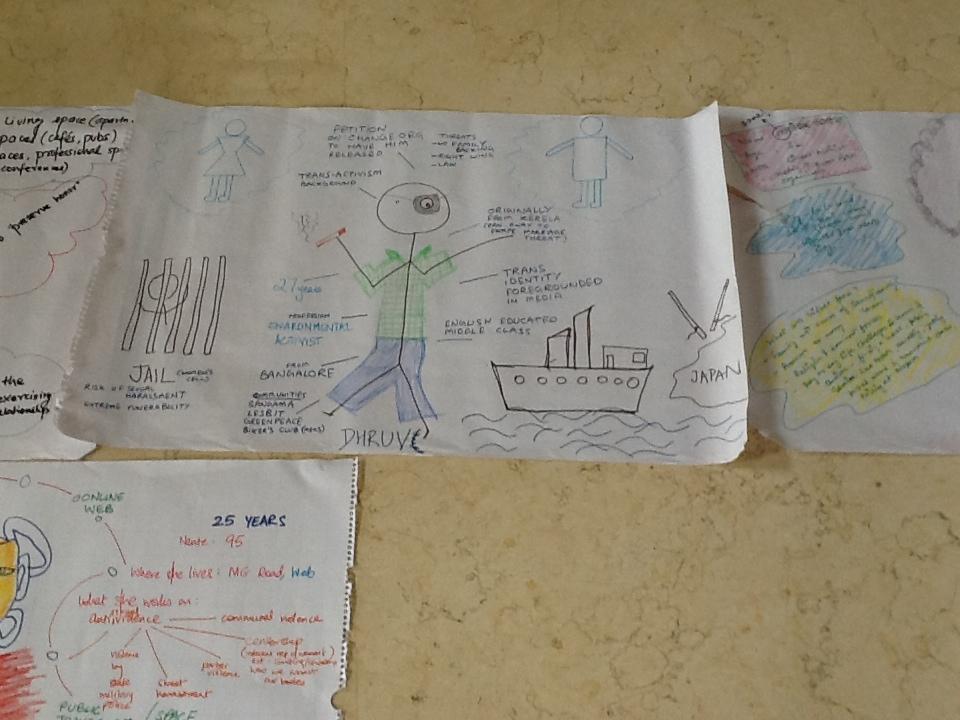
Imagine the life of an Indian gender or sexuality rights activist. What work do they do? Who do they interact with? What threats do they face? Here are some snapshots (created by participants):
31-year old Savita lives in Agra and works on issues relating to the Protection of Women from Domestic Violence Act (PWDVA) and interacts with the government, the police, lawyers, Muslim women’s groups, and sexuality rights groups. She faces threats from khap panchayat leaders, her natal family, and the police. Some of her biggest fears are her husband leaving her, her woman lover leaving her, violence at home, and stalking.
This nameless, gender-unspecified queer activist lives in a small, semi-urban location, where the queer community meets in secret. This person faces difficulties using public transport and finding housing, faces constant pressure to marry, and fears that their family will learn of their gender or sexual identity.
Because they work with vulnerable groups or are from marginalized sexual orientations or gender identities themselves, gender rights activists face many threats to their personal safety. These threats can range from very personal to those made by large institutions. And the more someone knows about you, the easier it is to threaten you. Where you work. How you travel there. A home address. A contact list of phone numbers. Whether it’s hiding one’s sexual orientation from family members, fearing violence from the police, or fears of stalking, the data about ourselves that is available to others can be used to attack us. But just how much of our personal information is out there?
Check out www.myshadow.org‘s ‘Trace My Shadow’”, which is an interactive visualization of how much of your data is available; how much of a trace you leave behind. From purchasing a certain computer to registering for a mobile phone to buying something online, various things that are a part of our daily lives are leaving behind a trail of information – leading right to us. We do many of these things without thinking about them, but the threats they post to our safety and security can be very real indeed.
For example, says Jac sm Kee from APC Women, ‘We often use our cell phones to take photos, and with that [comes] geo-locations that place where you are. So if you are already being threatened’ this is potentially dangerous. ‘When you get your phone or computer, it comes with everything turned on’, but by building awareness about what the security risks are, you know what you can do to prevent or minimize that risk. My Shadow provides various tool kits and guides to teach you where your data is unprotected, and how to minimize risks where possible. The way we handle our personal information is key to protecting ourselves and those we work with – and being aware of just how much is out there is the first step to making sure no one gets their hands on it.
One of the major places where we end up disclosing data about ourselves is on social networking sites. So take a moment to think about what sort of information about you is available on Facebook, for example. From contact details to addresses to relationship statuses to your sexual orientation, there’s a lot of stuff out there – stuff that you may not want everyone to see. And because social networks do what they say on the tin – they are networks of people you are connected to – it means that without proper security, it’s not only you, but also those around you, who are at risk. One way to minimise this risk is to create strong passwords – even for organizational accounts – that no one else has access to. Next, look at your friends list, and think about your relationships with these people. How many of them do you want seeing everything you do online? Facebook allows you to create different lists for different people, and for each list you can specify exactly what is okay and not okay for them to see. You can also limit who can see your activity log, past posts, and photographs. This may take some time to set up, since you’ll have the change the settings for each person, but if you are serious about keeping your personal information personal, it is worth it. Check out these security guides for Facebook, Twitter: and other social networks: by the Tactical Technology Collective.
Stay tuned for the next two blog posts for more concrete tips and tactics for your digital security.
- 7496 views





Add new comment